Corporate Accountability News Highlights is a regular series by Ranking Digital Rights that highlights key news related to tech companies, freedom of expression, and privacy issues around the world.
Social media censorship on the rise in China following death of Liu Xiaobo
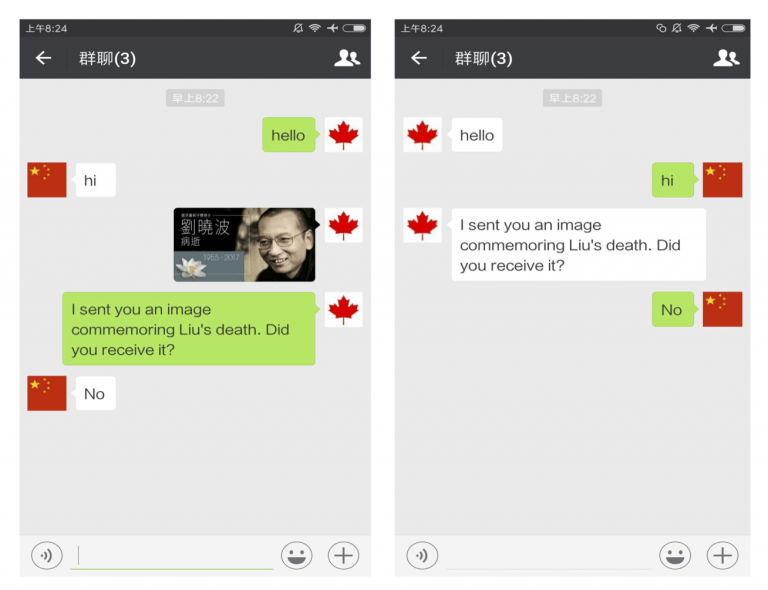
From Citizen Lab’s report: “Evidence of image censorship on WeChat’s group chat. A user with an international account attempts to send an image commemorating Liu Xiaobo’s death in a group chat. Users with China accounts in the group did not receive the message.” (Licensed CC BY 2.5 CA)
In China, online censorship of content related to human rights activist Liu Xiaobo has increased following his recent death, according to new research from Citizen Lab. Although certain terms relating to Liu have regularly been blocked, researchers found an increase in censorship of images and keywords on Chinese messaging app WeChat and social media platform Sina Weibo. According to the report, “the death of Liu marks a particularly critical moment for the Communist Party of China (CPC) and, as a result, Chinese Internet companies are facing direct or indirect government pressure to apply broad restrictions to content related to Liu.”
On July 18, users in China also reported issues using messaging app WhatsApp. The Guardian reports that photo, video, and voice messages sent from China using the services were blocked, but text messages were not. According to the BBC, neither the Chinese government nor WhatsApp have commented on the issue. As noted in the 2017 Corporate Accountability Index, Chinese companies are held liable if forbidden content is published on or transmitted through their services. Services that do not make a concerted effort to police such content are blocked from being accessed in China.
New HRW report highlights Russian government’s crackdown on freedom of expression
Russian authorities are increasing restrictions on freedom of expression online as part of a broader crackdown on civil society, according to a new report from Human Rights Watch. The report documents how Russian authorities are using “anti-extremism” laws to prosecute individuals for online speech, particularly those critical of the government, or those who post about sensitive topics, like the occupation of Crimea. The report urges the Russian government to refrain from requiring social media users to register with their real names. It also recommends the government repeal legislation that requires telecommunications and internet companies to store communications data for six months and metadata for up to three years, potentially allowing for authorities to access this information. The report also urges companies to regularly publish transparency reports detailing the number of government requests to censor content and to hand over user information, and the number of requests with which they comply; and minimizing the amount of user information stored within Russia, thereby minimizing the amount of user information that can potentially be accessed by authorities.
The 2017 Index findings showed that although Russian authorities have tightened controls over the internet, there are specific areas in which Russian companies can be more transparent about their policies affecting users’ freedom of expression rights, despite legal and political constraints. Both Russian companies evaluated—Mail.Ru and Yandex—disclosed little information about they handle government or private requests to block content or restrict user accounts, and neither published any data about the number of government requests it receives or with which it complies—although there are no laws prohibiting Russian companies from doing so.
Verizon responds to vendor data breach
U.S. telecommunications company Verizon has confirmed a recent data breach affecting millions of customer accounts. According to ZDNet, the breach occurred after a vendor contracted by Verizon uploaded personal information belonging to at least 14 million subscribers to an unprotected cloud storage server. A security researcher discovered the vulnerability and notified Verizon, but the vulnerability remained unpatched for more than a week, according to the Washington Post. After the researcher then followed up with the company’s cyber emergency team, noting he had raised the issue a week earlier, Verizon told him the issue would be addressed, and the vendor fixed the vulnerability within a day. “The informal contact did not drive the action we would have wanted to see and we are reviewing opportunities for improving our handling of such contacts,” company spokesperson David Samberg said.
In response to the rise in data breaches, RDR added an indicator on data breaches to our methodology evaluating whether companies clearly disclose their policies for responding to a data breach before one occurs. We expect companies to clearly disclose that they will immediately notify the relevant authorities, as well as their processes for notifying data subjects who might be affected by a data breach, and what kinds of steps they will take to address the impact of a data breach on users. Companies should also clearly disclose that they have a mechanism through which security researchers can submit vulnerabilities they discover, as well as the timeframe in which they will review reports of vulnerabilities. Our findings showed that although 11 companies disclosed they had such a mechanism, only six clearly disclosed the timeline in which they commit to review reports.




